Moodle 3.9.11+ was recently installed in Azure Cloud. The installation was not an easy ride because Moodle was not prepared to install the application behind an SSL proxy. You may find the solution for this here: Installing Moodle using SSL Proxy.
I started to use Moodle then I realize that I cannot add an activity or resource. And this is something that without this feature Moodle is useless. So first of all, I checked the Javascript console on the client-side and I’d found that some of the Javascript could not be loaded because the response was 403 Forbidden.
The error message was:
Failed to load resource: the server responded with a status 403 (ModSecurity Action)
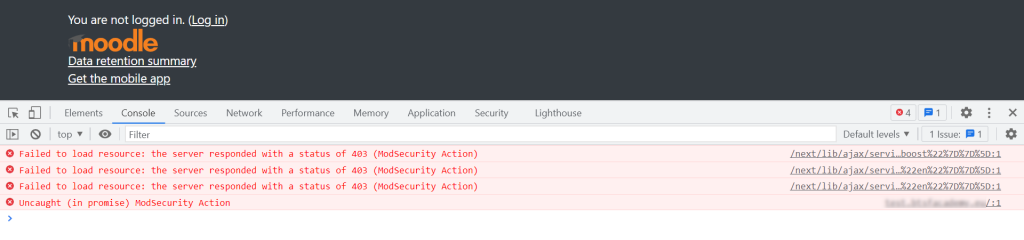
If I opened the resource in the browser I got the 403 Forbidden Windowsish style of error so because my webserver is a Linux server I’d realized that the issue is on the Azure Application Gateway side. It should block something that it should not have.
I made some Google searches on what could block the Moodle call and another search on how to check the Azure Application Firewall logs.
On the Moodle Forums, I’d found a post from Roberto Sbravati who had the same issue. He listed three Azure WAF rules that he had to disable.
This had confirmed that I need to check the WAF logs. I had found another article on the Microsoft document site which was helping me. The page was the “Use Log Analytics to examine Application Gateway Web Application Firewall (WAF) Logs“. It helped me to identify which rule blocks Moodle.
For that, you need to open your Azure portal. Select the Application Gateway and click on the logs on the left.
Here you need to use Azure Data Explorer Query Language which is based on the Kusto Query Language. Microsoft offers some tutorials. On the Use Log Analytics to examine Application Gateway Web Application Firewall (WAF) Logs page you may find the query which is the:
AzureDiagnostics
| where ResourceProvider == "MICROSOFT.NETWORK" and Category == "ApplicationGatewayFirewallLog"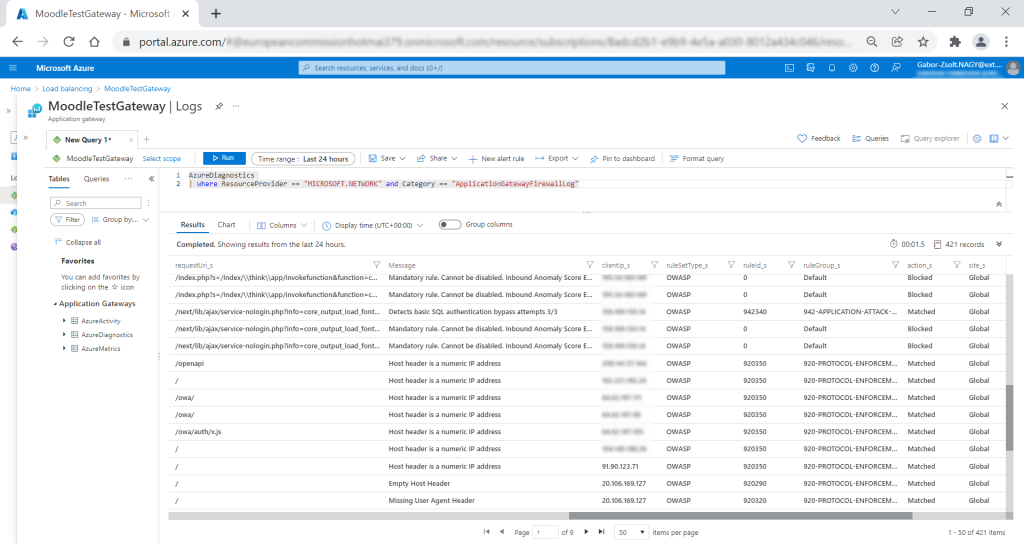
Here I could see that WAF blocks Moodle because of rule 942340 which is a bit funny because this rule is for SQL injection and there is nothing in the request which points to that. However, in my case, I had to switch off this rule.
To turn this rule off you need to navigate to the Application Gateway and click on the Web application firewall on the left then click on the Rules. In the search box type 942340 and then untick the Enable box. Save the modifications.
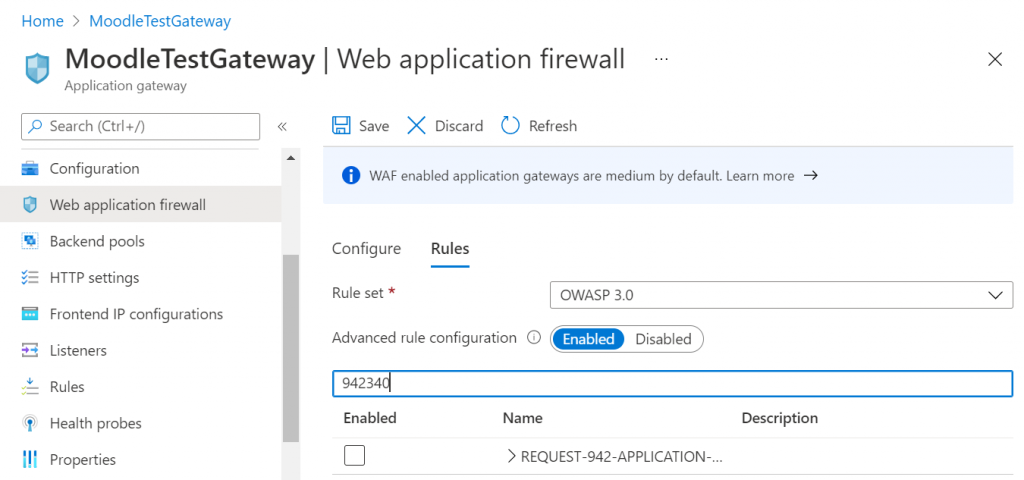
By turning off this rule, your Moodle site will not be vulnerable.
And now you are ready to use your Moodle without Javascript errors.
Cheers,